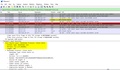
How to stop Firefox from sending TLS 1.0 even after disabled in settings.
Currently running Firefox 73.0.1.
Connections to my server from Firefox all fail with 'connection_reset' from the server.
Wireshark capture shows that Firefox is attempting a 'Client Hello' using TLS 1.0.
Servers are configured with TLS 1.0 removed/disabled.
All the Firefox advanced settings in about:config are set with TLS 1.2 as the minimum, yet Firefox insists on sending TLS 1.0 'client hello'.
Not an expert, but it kind of looks like Firefox is sending a TLS 1.2 'Client Hello' encapsulated inside a TLS 1.0 'Client Hello'? Is this even possible?
Chrome, IE, and Edge behave appropriately and send 'Client Hello' as TLS 1.2.
How do we get Firefox to send the appropriate 'Client Hello'?
This affects multiple versions of Firefox, even the beta builds that I tested over the weekend and occurs on any machine tested so far. Windows 10, various flavors of Linux, etc.
See screenshots below for configuration settings and wireshark capture.
Thanks for the help!
Krejt Përgjigjet (4)
What about security.tls.hello_downgrade_check?
Thank you for the help!
When I attempted the connection earlier, security.tls.hello_downgrade_check was set to the default of 'true'.
I changed security.tls.hello_downgrade_check to be 'false', went to 'Preferences | Privacy & Security | Cookies and Site Data' and cleared all data. Then I closed the browser and rebooted the VM.
Still I get a TLS1.0 'Client Hello' just as before.
Mike Leimer said
Then I closed the browser and rebooted the VM.
Is there anything in the VM that might be proxying the connection from Firefox?
Sorry for the added confusion there, nothing is set up to proxy the VM, networking is set up to NAT my workstation network connection.
Additionally, I see the same behavior on any of the physical machines that I have tested on as well.
I have just been using a VM on my workstation for convenience and to grab the screenshots for this post, but the behavior is identical to physical PC's in this context.
- As an interesting note, during this troubleshooting I did install Fiddler on one of the physical workstations.
Using Fiddler as a proxy, the Wireshark capture *does* show a TLS1.2 'Client Hello' and the connections to my website *does* complete successfully, so it appears that Fiddler is sending the appropriate TLS1.2 request on behalf of Firefox. I'm not sure if this means anything, or nothing but I thought I'd share it as a data point.