plugins could not be verified firefox esr 52
I'm using Firefox ESR 52.9 because it is the latest version that the Pocket extension still works with. It just suddenly (without any updates or warning) disabled the AdBlock Plus, Roboform, and Google Shortcuts extensions (all of which were working perfectly fine yesterday) because "they cannot be verified." and it isn't giving me the option to re-enable them.
The info at https://support.mozilla.org/en-US/kb/add-ons-disabled-or-fail-to-install-firefox?redirectlocale=en-US&redirectslug=add-ons-failing-install-firefox and https://blog.mozilla.org/addons/2019/05/04/update-regarding-add-ons-in-firefox/ is not helpful because the verison of Firefox I have doesn't show the studies option that is referenced there.
And an update that is to Firefox ESR 53 or later also isn't useful because then my old Pocket extension won't work (and that extension is KEY for me). Please provide an immediate fix for Firefox ESR 52.9.
Opaite Mbohovái (20)
Sorry, a critical certificate used to verify extension signatures expired, which causes many of them to be distrusted. There is a hotfix patch out going out for the past 8 hours to current versions of Firefox (Win/Mac/Linux), but Firefox 52 is no longer supported so you probably have to try something a bit different.
I have not had the chance to set up Firefox 52 ESR to try it myself, but the extension which is being pushed out can be "sideloaded" from here:
Does that work on your Firefox?
Unfortunately no. After (successfully) installing it I restarted firefox, but the 3 add-ons still show disabled because they can't be verified.
FWIW, I've been asking Pocket/Mozilla support for several years now to update or replace the old pocket extension (that allows syncing and save all tabs to Pocket) so that the old functionality is available with the latest Firefox (which would allow me to update to the latest), but it hasn't been a priority :(
Well, you could try a Browser Console script that temporarily marks extensions as not needing verification. It worked on Firefox 66 in a quick test, but I don't know whether there are any side effects or whether it would work on Firefox 52.
Unfortunately that doesn't work either - it gives
IndexedDB UnknownErr: ActorsParent.cpp:599 (unknown) UnknownError indexed-db.js:59:9 A promise chain failed to handle a rejection. Did you forget to '.catch', or did you forget to 'return'? See https://developer.mozilla.org/Mozilla/JavaScript_code_modules/Promise.jsm/Promise
Date: Sat May 04 2019 17:05:21 GMT-0400 (Eastern Standard Time) Full Message: undefined Full Stack: JS frame :: resource://gre/modules/Promise.jsm -> resource://gre/modules/Promise-backend.js :: PendingErrors.register :: line 194 JS frame :: resource://gre/modules/Promise.jsm -> resource://gre/modules/Promise-backend.js :: this.PromiseWalker.completePromise :: line 715 JS frame :: resource://gre/modules/commonjs/toolkit/loader.js -> resource://devtools/shared/async-storage.js :: withStoreOnError :: line 60
jscher2000 said
Sorry, a critical certificate used to verify extension signatures expired, which causes many of them to be distrusted. There is a hotfix patch out going out for the past 8 hours to current versions of Firefox (Win/Mac/Linux), but Firefox 52 is no longer supported so you probably have to try something a bit different. I have not had the chance to set up Firefox 52 ESR to try it myself, but the extension which is being pushed out can be "sideloaded" from here: https://storage.googleapis.com/moz-fx-normandy-prod-addons/extensions/hotfix-update-xpi-intermediate%40mozilla.com-1.0.2-signed.xpi Does that work on your Firefox?
Oh, you mean your guys know how to BREAK 55 and NOT fix it? That's nonsense. They want to FORCE us to upgrade.
UPDATE: Mozilla is working on a solution for older versions of Firefox, and this workaround is both unofficial and unsupported. It is possible it might need to be backed out if a different approach eventually is deployed.
Sorry, we're having to get a little more basic. Do you want to try this:
Overview
(1) Install the certificate the hotfix would have installed (2) Trigger Firefox to re-verify your extensions (3) Wait until it is back to normal
Steps
(1) Install certificate
I extracted the certificate from my Firefox 66 and saved it on my webserver. Obviously if you don't trust me, you should not install it.
Two possible methods: click to download through the certificate installer, or right-click > Save Link As to save a local copy and then import it.
https://www.jeffersonscher.com/sumo/signingca1addonsmozillaorg_20190504.crt
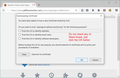
Screenshot #1 shows the download method. Don't check any of the boxes, just click OK.
To import instead:
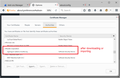
Go to the Options/Preferences page, Advanced section, Certificates panel, then click Certificate Manager. Make sure the Authorities tab is selected, then click Import. Find the file you downloaded and open it, then you should get the same dialog as in Screenshot #1, don't check any of the boxes, just click OK. Then you should see the new cert in the list in the Certificate Manager, as shown in Screenshot #2.
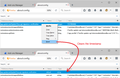
(2) Clear the time Firefox last re-verified
This will set Firefox up to check much sooner than it otherwise would check.
(A) In a new tab, type or paste about:config in the address bar and press Enter/Return. Click the button promising to be careful or accepting the risk.
(B) In the search box above the list, type or paste xpi- and pause while the list is filtered
(C) Right-click the app.update.lastUpdateTime.xpi-signature-verification preference and click Reset on the context menu
Screenshot #3 illustrates the expected result.
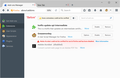
(3) Restart Firefox
You can exit Firefox normally, then start it up again. In my tests, it took less than 60 seconds for Firefox to verify my extensions. Screenshot #4 is "before" and Screenshot #5 is "after."
Hopefully that will work for you.
Moambuepyre
Note that in Firefox 52 ESR you can disable signature for extensions
- xpinstall.signatures.require = false
You can open the about:config page via the location/address bar. You can accept the warning and click "I accept the risk!" to continue.
You can alternatively add the certificate in Firefox 52with this code in the Browser Console.
You will also have to reset this pref on the about:config page to trigger a signature check.
- app.update.lastUpdateTime.xpi-signature-verification
try {
let intermediate = "MIIHLTCCBRWgAwIBAgIDEAAIMA0GCSqGSIb3DQEBDAUAMH0xCzAJBgNVBAYTAlVTMRwwGgYDVQQKExNNb3ppbGxhIENvcnBvcmF0aW9uMS8wLQYDVQQLEyZNb3ppbGxhIEFNTyBQcm9kdWN0aW9uIFNpZ25pbmcgU2VydmljZTEfMB0GA1UEAxMWcm9vdC1jYS1wcm9kdWN0aW9uLWFtbzAeFw0xNTA0MDQwMDAwMDBaFw0yNTA0MDQwMDAwMDBaMIGnMQswCQYDVQQGEwJVUzEcMBoGA1UEChMTTW96aWxsYSBDb3Jwb3JhdGlvbjEvMC0GA1UECxMmTW96aWxsYSBBTU8gUHJvZHVjdGlvbiBTaWduaW5nIFNlcnZpY2UxJjAkBgNVBAMTHXNpZ25pbmdjYTEuYWRkb25zLm1vemlsbGEub3JnMSEwHwYJKoZIhvcNAQkBFhJmb3hzZWNAbW96aWxsYS5jb20wggIiMA0GCSqGSIb3DQEBAQUAA4ICDwAwggIKAoICAQC/qluiiI+wO6qGA4vH7cHvWvXpdju9JnvbwnrbYmxhtUpfS68LbdjGGtv7RP6F1XhHT4MU3v4GuMulH0E4Wfalm8evsb3tBJRMJPICJX5UCLi6VJ6J2vipXSWBf8xbcOB+PY5Kk6L+EZiWaepiM23CdaZjNOJCAB6wFHlGe+zUk87whpLa7GrtrHjTb8u9TSS+mwjhvgfP8ILZrWhzb5H/ybgmD7jYaJGIDY/WDmq1gVe03fShxD09Ml1P7H38o5kbFLnbbqpqC6n8SfUI31MiJAXAN2e6rAOM8EmocAY0EC5KUooXKRsYvHzhwwHkwIbbe6QpTUlIqvw1MPlQPs7Zu/MBnVmyGTSqJxtYoklr0MaEXnJNY3g3FDf1R0Opp2/BEY9Vh3Fc9Pq6qWIhGoMyWdueoSYa+GURqDbsuYnk7ZkysxK+yRoFJu4x3TUBmMKM14jQKLgxvuIzWVn6qg6cw7ye/DYNufc+DSPSTSakSsWJ9IPxiAU7xJ+GCMzaZ10Y3VGOybGLuPxDlSd6KALAoMcl9ghB2mvfB0N3wv6uWnbKuxihq/qDps+FjliNvr7C66mIVH+9rkyHIy6GgIUlwr7E88Qqw+SQeNeph6NIY85PL4p0Y8KivKP4J928tpp18wLuHNbIG+YaUk5WUDZ6/2621pi19UZQ8iiHxN/XKQIDAQABo4IBiTCCAYUwDAYDVR0TBAUwAwEB/zAOBgNVHQ8BAf8EBAMCAQYwFgYDVR0lAQH/BAwwCgYIKwYBBQUHAwMwHQYDVR0OBBYEFBY++xz/DCuT+JsV1y2jwuZ4YdztMIGoBgNVHSMEgaAwgZ2AFLO86lh0q+FueCqyq5wjHqhjLJe3oYGBpH8wfTELMAkGA1UEBhMCVVMxHDAaBgNVBAoTE01vemlsbGEgQ29ycG9yYXRpb24xLzAtBgNVBAsTJk1vemlsbGEgQU1PIFByb2R1Y3Rpb24gU2lnbmluZyBTZXJ2aWNlMR8wHQYDVQQDExZyb290LWNhLXByb2R1Y3Rpb24tYW1vggEBMDMGCWCGSAGG+EIBBAQmFiRodHRwOi8vYWRkb25zLm1vemlsbGEub3JnL2NhL2NybC5wZW0wTgYDVR0eBEcwRaFDMCCCHi5jb250ZW50LXNpZ25hdHVyZS5tb3ppbGxhLm9yZzAfgh1jb250ZW50LXNpZ25hdHVyZS5tb3ppbGxhLm9yZzANBgkqhkiG9w0BAQwFAAOCAgEAX1PNli/zErw3tK3S9Bv803RV4tHkrMa5xztxzlWja0VAUJKEQx7f1yM8vmcQJ9g5RE8WFc43IePwzbAoum5F4BTM7tqM//+e476F1YUgB7SnkDTVpBOnV5vRLz1Si4iJ/U0HUvMUvNJEweXvKg/DNbXuCreSvTEAawmRIxqNYoaigQD8x4hCzGcVtIi5Xk2aMCJW2K/6JqkN50pnLBNkPx6FeiYMJCP8z0FIz3fv53FHgu3oeDhi2u3VdONjK3aaFWTlKNiGeDU0/lr0suWfQLsNyphTMbYKyTqQYHxXYJno9PuNi7e1903PvM47fKB5bFmSLyzB1hB1YIVLj0/YqD4nz3lADDB91gMBB7vR2h5bRjFqLOxuOutNNcNRnv7UPqtVCtLF2jVb4/AmdJU78jpfDs+BgY/t2bnGBVFBuwqS2Kult/2kth4YMrL5DrURIM8oXWVQRBKxzr843yDmHo8+2rqxLnZcmWoe8yQ41srZ4IB+V3w2TIAd4gxZAB0Xa6KfnR4D8RgE5sgmgQoK7Y/hdvd9Ahu0WEZI8Eg+mDeCeojWcyjF+dt6c2oERiTmFTIFUoojEjJwLyIqHKt+eApEYpF7imaWcumFN1jR+iUjE4ZSUoVxGtZ/Jdnkf8VVQMhiBA+i7r5PsfrHq+lqTTGOg+GzYx7OmoeJAT0zo4c=";
let certDB = Cc["@mozilla.org/security/x509certdb;1"].getService(Ci.nsIX509CertDB);
certDB.addCertFromBase64(intermediate, "", "");
console.log("new intermediate certificate added");
} catch (e) {
console.error("failed to add new intermediate certificate:", e);
}
See also:
- /questions/1258275 How do I re-enable the add-ons WITHOUT being forced to upgrade
Moambuepyre
jscher2000 said
... Firefox 52 is no longer supported so you probably have to try something a bit different .... Does that work on your Firefox?
It appeared to download and install successfully. Closed and reopened FF 52. Nothing was fixed.
gnappi said
jscher2000 saidSorry, a critical certificate used to verify extension signatures expired, which causes many of them to be distrusted. There is a hotfix patch out going out for the past 8 hours to current versions of Firefox (Win/Mac/Linux), but Firefox 52 is no longer supported so you probably have to try something a bit different. I have not had the chance to set up Firefox 52 ESR to try it myself, but the extension which is being pushed out can be "sideloaded" from here: https://storage.googleapis.com/moz-fx-normandy-prod-addons/extensions/hotfix-update-xpi-intermediate%40mozilla.com-1.0.2-signed.xpi Does that work on your Firefox?Oh, you mean your guys know how to BREAK 55 and NOT fix it? That's nonsense. They want to FORCE us to upgrade.
THAT is my big concern. That may be what's behind this mess. We broke it, we can't fix it, so sorry, now go download the newest version.
Please, Mozilla, prove me wrong.
cor-el said
Note that in Firefox 52 ESR you can disable signature for extensions
- xpinstall.signatures.require = false ...
My signatures were already set to false, so that obviously did nothing. FFS, this is getting time consuming and frustrating.
cor-el said
You can alternatively add the certificate in Firefox 52with this code in the Browser Console.
try { let intermediate = "MIIHLTCCBRWgAwIBAgIDEAAIMA0GCSqGSIb3DQEBDAUAMH0xCzAJBgNVBAYTAlVTMRwwGgYDVQQKExNNb3ppbGxhIENvcnBvcmF0aW9uMS8wLQYDVQQLEyZNb3ppbGxhIEFNTyBQcm9kdWN0aW9uIFNpZ25pbmcgU2VydmljZTEfMB0GA1UEAxMWcm9vdC1jYS1wcm9kdWN0aW9uLWFtbzAeFw0xNTA0MDQwMDAwMDBaFw0yNTA0MDQwMDAwMDBaMIGnMQswCQYDVQQGEwJVUzEcMBoGA1UEChMTTW96aWxsYSBDb3Jwb3JhdGlvbjEvMC0GA1UECxMmTW96aWxsYSBBTU8gUHJvZHVjdGlvbiBTaWduaW5nIFNlcnZpY2UxJjAkBgNVBAMTHXNpZ25pbmdjYTEuYWRkb25zLm1vemlsbGEub3JnMSEwHwYJKoZIhvcNAQkBFhJmb3hzZWNAbW96aWxsYS5jb20wggIiMA0GCSqGSIb3DQEBAQUAA4ICDwAwggIKAoICAQC/qluiiI+wO6qGA4vH7cHvWvXpdju9JnvbwnrbYmxhtUpfS68LbdjGGtv7RP6F1XhHT4MU3v4GuMulH0E4Wfalm8evsb3tBJRMJPICJX5UCLi6VJ6J2vipXSWBf8xbcOB+PY5Kk6L+EZiWaepiM23CdaZjNOJCAB6wFHlGe+zUk87whpLa7GrtrHjTb8u9TSS+mwjhvgfP8ILZrWhzb5H/ybgmD7jYaJGIDY/WDmq1gVe03fShxD09Ml1P7H38o5kbFLnbbqpqC6n8SfUI31MiJAXAN2e6rAOM8EmocAY0EC5KUooXKRsYvHzhwwHkwIbbe6QpTUlIqvw1MPlQPs7Zu/MBnVmyGTSqJxtYoklr0MaEXnJNY3g3FDf1R0Opp2/BEY9Vh3Fc9Pq6qWIhGoMyWdueoSYa+GURqDbsuYnk7ZkysxK+yRoFJu4x3TUBmMKM14jQKLgxvuIzWVn6qg6cw7ye/DYNufc+DSPSTSakSsWJ9IPxiAU7xJ+GCMzaZ10Y3VGOybGLuPxDlSd6KALAoMcl9ghB2mvfB0N3wv6uWnbKuxihq/qDps+FjliNvr7C66mIVH+9rkyHIy6GgIUlwr7E88Qqw+SQeNeph6NIY85PL4p0Y8KivKP4J928tpp18wLuHNbIG+YaUk5WUDZ6/2621pi19UZQ8iiHxN/XKQIDAQABo4IBiTCCAYUwDAYDVR0TBAUwAwEB/zAOBgNVHQ8BAf8EBAMCAQYwFgYDVR0lAQH/BAwwCgYIKwYBBQUHAwMwHQYDVR0OBBYEFBY++xz/DCuT+JsV1y2jwuZ4YdztMIGoBgNVHSMEgaAwgZ2AFLO86lh0q+FueCqyq5wjHqhjLJe3oYGBpH8wfTELMAkGA1UEBhMCVVMxHDAaBgNVBAoTE01vemlsbGEgQ29ycG9yYXRpb24xLzAtBgNVBAsTJk1vemlsbGEgQU1PIFByb2R1Y3Rpb24gU2lnbmluZyBTZXJ2aWNlMR8wHQYDVQQDExZyb290LWNhLXByb2R1Y3Rpb24tYW1vggEBMDMGCWCGSAGG+EIBBAQmFiRodHRwOi8vYWRkb25zLm1vemlsbGEub3JnL2NhL2NybC5wZW0wTgYDVR0eBEcwRaFDMCCCHi5jb250ZW50LXNpZ25hdHVyZS5tb3ppbGxhLm9yZzAfgh1jb250ZW50LXNpZ25hdHVyZS5tb3ppbGxhLm9yZzANBgkqhkiG9w0BAQwFAAOCAgEAX1PNli/zErw3tK3S9Bv803RV4tHkrMa5xztxzlWja0VAUJKEQx7f1yM8vmcQJ9g5RE8WFc43IePwzbAoum5F4BTM7tqM//+e476F1YUgB7SnkDTVpBOnV5vRLz1Si4iJ/U0HUvMUvNJEweXvKg/DNbXuCreSvTEAawmRIxqNYoaigQD8x4hCzGcVtIi5Xk2aMCJW2K/6JqkN50pnLBNkPx6FeiYMJCP8z0FIz3fv53FHgu3oeDhi2u3VdONjK3aaFWTlKNiGeDU0/lr0suWfQLsNyphTMbYKyTqQYHxXYJno9PuNi7e1903PvM47fKB5bFmSLyzB1hB1YIVLj0/YqD4nz3lADDB91gMBB7vR2h5bRjFqLOxuOutNNcNRnv7UPqtVCtLF2jVb4/AmdJU78jpfDs+BgY/t2bnGBVFBuwqS2Kult/2kth4YMrL5DrURIM8oXWVQRBKxzr843yDmHo8+2rqxLnZcmWoe8yQ41srZ4IB+V3w2TIAd4gxZAB0Xa6KfnR4D8RgE5sgmgQoK7Y/hdvd9Ahu0WEZI8Eg+mDeCeojWcyjF+dt6c2oERiTmFTIFUoojEjJwLyIqHKt+eApEYpF7imaWcumFN1jR+iUjE4ZSUoVxGtZ/Jdnkf8VVQMhiBA+i7r5PsfrHq+lqTTGOg+GzYx7OmoeJAT0zo4c="; let certDB = Cc["@mozilla.org/security/x509certdb;1"].getService(Ci.nsIX509CertDB); certDB.addCertFromBase64(intermediate, "", ""); console.log("new intermediate certificate added"); } catch (e) { console.error("failed to add new intermediate certificate:", e); }
See also:
- /questions/1258275 How do I re-enable the add-ons WITHOUT being forced to upgrade
Also did not work.
PS: Actually, it was added. It just didn't fix anything. Closed reopened yada yada yada
Moambuepyre
jscher2000 said
Sorry, we're having to get a little more basic. Do you want to try this: Overview (1) Install the certificate the hotfix would have installed (2) Trigger Firefox to re-verify your extensions (3) Wait until it is back to normal ... Hopefully that will work for you.
That seems to have worked. THANK YOU VERY MUCH.
Setting xpinstall.signatures.require = false worked (yay)!
Before that I tried this to install the intermediate
try {
let intermediate = "MIIHLTCCBRWgAwIBAgIDEAAIMA0GCSqGSIb3DQEBDAUAMH0xCzAJBgNVBAYTAlVTMRwwGgYDVQQKExNNb3ppbGxhIENvcnBvcmF0aW9uMS8wLQYDVQQLEyZNb3ppbGxhIEFNTyBQcm9kdWN0aW9uIFNpZ25pbmcgU2VydmljZTEfMB0GA1UEAxMWcm9vdC1jYS1wcm9kdWN0aW9uLWFtbzAeFw0xNTA0MDQwMDAwMDBaFw0yNTA0MDQwMDAwMDBaMIGnMQswCQYDVQQGEwJVUzEcMBoGA1UEChMTTW96aWxsYSBDb3Jwb3JhdGlvbjEvMC0GA1UECxMmTW96aWxsYSBBTU8gUHJvZHVjdGlvbiBTaWduaW5nIFNlcnZpY2UxJjAkBgNVBAMTHXNpZ25pbmdjYTEuYWRkb25zLm1vemlsbGEub3JnMSEwHwYJKoZIhvcNAQkBFhJmb3hzZWNAbW96aWxsYS5jb20wggIiMA0GCSqGSIb3DQEBAQUAA4ICDwAwggIKAoICAQC/qluiiI+wO6qGA4vH7cHvWvXpdju9JnvbwnrbYmxhtUpfS68LbdjGGtv7RP6F1XhHT4MU3v4GuMulH0E4Wfalm8evsb3tBJRMJPICJX5UCLi6VJ6J2vipXSWBf8xbcOB+PY5Kk6L+EZiWaepiM23CdaZjNOJCAB6wFHlGe+zUk87whpLa7GrtrHjTb8u9TSS+mwjhvgfP8ILZrWhzb5H/ybgmD7jYaJGIDY/WDmq1gVe03fShxD09Ml1P7H38o5kbFLnbbqpqC6n8SfUI31MiJAXAN2e6rAOM8EmocAY0EC5KUooXKRsYvHzhwwHkwIbbe6QpTUlIqvw1MPlQPs7Zu/MBnVmyGTSqJxtYoklr0MaEXnJNY3g3FDf1R0Opp2/BEY9Vh3Fc9Pq6qWIhGoMyWdueoSYa+GURqDbsuYnk7ZkysxK+yRoFJu4x3TUBmMKM14jQKLgxvuIzWVn6qg6cw7ye/DYNufc+DSPSTSakSsWJ9IPxiAU7xJ+GCMzaZ10Y3VGOybGLuPxDlSd6KALAoMcl9ghB2mvfB0N3wv6uWnbKuxihq/qDps+FjliNvr7C66mIVH+9rkyHIy6GgIUlwr7E88Qqw+SQeNeph6NIY85PL4p0Y8KivKP4J928tpp18wLuHNbIG+YaUk5WUDZ6/2621pi19UZQ8iiHxN/XKQIDAQABo4IBiTCCAYUwDAYDVR0TBAUwAwEB/zAOBgNVHQ8BAf8EBAMCAQYwFgYDVR0lAQH/BAwwCgYIKwYBBQUHAwMwHQYDVR0OBBYEFBY++xz/DCuT+JsV1y2jwuZ4YdztMIGoBgNVHSMEgaAwgZ2AFLO86lh0q+FueCqyq5wjHqhjLJe3oYGBpH8wfTELMAkGA1UEBhMCVVMxHDAaBgNVBAoTE01vemlsbGEgQ29ycG9yYXRpb24xLzAtBgNVBAsTJk1vemlsbGEgQU1PIFByb2R1Y3Rpb24gU2lnbmluZyBTZXJ2aWNlMR8wHQYDVQQDExZyb290LWNhLXByb2R1Y3Rpb24tYW1vggEBMDMGCWCGSAGG+EIBBAQmFiRodHRwOi8vYWRkb25zLm1vemlsbGEub3JnL2NhL2NybC5wZW0wTgYDVR0eBEcwRaFDMCCCHi5jb250ZW50LXNpZ25hdHVyZS5tb3ppbGxhLm9yZzAfgh1jb250ZW50LXNpZ25hdHVyZS5tb3ppbGxhLm9yZzANBgkqhkiG9w0BAQwFAAOCAgEAX1PNli/zErw3tK3S9Bv803RV4tHkrMa5xztxzlWja0VAUJKEQx7f1yM8vmcQJ9g5RE8WFc43IePwzbAoum5F4BTM7tqM//+e476F1YUgB7SnkDTVpBOnV5vRLz1Si4iJ/U0HUvMUvNJEweXvKg/DNbXuCreSvTEAawmRIxqNYoaigQD8x4hCzGcVtIi5Xk2aMCJW2K/6JqkN50pnLBNkPx6FeiYMJCP8z0FIz3fv53FHgu3oeDhi2u3VdONjK3aaFWTlKNiGeDU0/lr0suWfQLsNyphTMbYKyTqQYHxXYJno9PuNi7e1903PvM47fKB5bFmSLyzB1hB1YIVLj0/YqD4nz3lADDB91gMBB7vR2h5bRjFqLOxuOutNNcNRnv7UPqtVCtLF2jVb4/AmdJU78jpfDs+BgY/t2bnGBVFBuwqS2Kult/2kth4YMrL5DrURIM8oXWVQRBKxzr843yDmHo8+2rqxLnZcmWoe8yQ41srZ4IB+V3w2TIAd4gxZAB0Xa6KfnR4D8RgE5sgmgQoK7Y/hdvd9Ahu0WEZI8Eg+mDeCeojWcyjF+dt6c2oERiTmFTIFUoojEjJwLyIqHKt+eApEYpF7imaWcumFN1jR+iUjE4ZSUoVxGtZ/Jdnkf8VVQMhiBA+i7r5PsfrHq+lqTTGOg+GzYx7OmoeJAT0zo4c=";
let certDB = Cc["@mozilla.org/security/x509certdb;1"].getService(Ci.nsIX509CertDB);
certDB.addCertFromBase64(intermediate, "", "");
console.log("new intermediate certificate added");
} catch (e) {
console.error("failed to add new intermediate certificate:", e);
}
failed with: undefined IndexedDB UnknownErr: ActorsParent.cpp:599 (unknown) UnknownError
Disabling certificate
Users could install this "hot-fix" extension to get the fix that Mozilla has done.
Worked for me with Firefox 66.0.3 and supposedly it is supposed to work for all older versions, too; although I am not able to verify that.
the-edmeister said
Users could install this "hot-fix" extension to get the fix that Mozilla has done. Worked for me with Firefox 66.0.3 and supposedly it is supposed to work for all older versions, too; although I am not able to verify that.
I tested the extension in 52 ESR, and it errored out.
cor-el said
Note that in Firefox 52 ESR you can disable signature for extensionsYou can open the about:config page via the location/address bar. You can accept the warning and click "I accept the risk!" to continue.
- xpinstall.signatures.require = false
Cor-el, that does it, it re-enabled all the disabled extensions. So for older versions of FF the fix takes about 20 seconds.
Of the 4 extensions that were disabled, 3 are working properly and 1 seems to be broken, it functions but doesn't retain log in info.
Of course now the question is, for how long we leave signatures disabled.
Hi elzach, the risk with that setting is possibly installing extensions that have never undergone even an automated code review, or installing a rogue update. Obviously you control your own installation of new extensions. To block extension auto-updates, you can use this preference:
(1) In a new tab, type or paste about:config in the address bar and submit that. Click the button promising to be careful or accepting the risk if presented.
(2) In the search box above the list, type or paste autoup and pause while the list is filtered
(3) Double-click the extensions.update.autoUpdateDefault preference to switch it from true to false
With that change, the Add-ons page will show a new "Updates Available" section in the left column when updates are detected so you can examine them individually before updating them.
elzach said
cor-el saidNote that in Firefox 52 ESR you can disable signature for extensionsYou can open the about:config page via the location/address bar. You can accept the warning and click "I accept the risk!" to continue.
- xpinstall.signatures.require = false
Cor-el, that does it, it re-enabled all the disabled extensions. So for older versions of FF the fix takes about 20 seconds.
Of the 4 extensions that were disabled, 3 are working properly and 1 seems to be broken, it functions but doesn't retain log in info.
Of course now the question is, for how long we leave signatures disabled.
I was set to "false" before armag-addon occurred. Still am...I czeched. Still have several DOA add-ons, ABP is one, need 3.0.3 so Element Helper works. "Updates Available" shows now in add-ons, but you KNOW it will update me to a later version. Last night, I even tried, and connection failed. Still not "fixed".